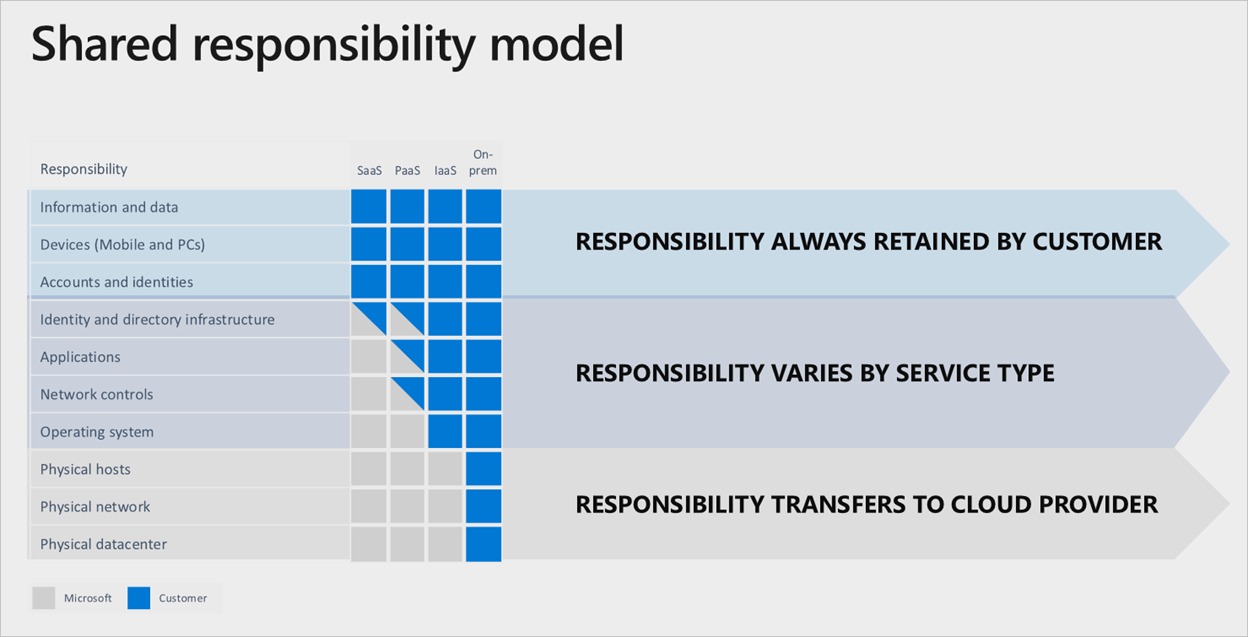
The Shared Responsibility Model is a cloud security framework that delineates the obligations of cloud computing providers and its customers to disseminate accountability.
Cloud is easy. It’s easy to spin up a virtual machine, easy to power it on, easy to install an application, easy to add internet access, and easy to remotely connect for the first time. Cloud providers made it easy for you to sign up, easy to create expensive resources with just a click.
The shared responsibility model for cloud security is one of those things that seems simple enough on the surface but is actually very complex when putting it into practice. Security will tend to be an afterthought for a large portion of users deploying workloads to the cloud. Adhering to a shared security responsibility model, means your security team maintains responsibilities for security as you move applications, data, containers, and workloads to the cloud, while the provider takes some responsibility, but not much.
Unpacking your responsibilities
Holding up your end of the shared responsibility bargain is easier said than done. Unlike traditional on-prem datacenter security the load of hardening the operating environment and physical servers may be gone but securing your applications and users becomes a much more elaborate process in the cloud. The key to a successful security implementation in a cloud environment is understanding where your provider’s responsibility ends, and where yours begins. Generally, cloud providers will stake claim to the hardware, software and core networking infrastructure that enable their cloud services.
Beyond the core operating environment, the securing of your users and applications will fall solely on you, the user. Security for things like data classification, network controls, and physical security need clear owners. This list is a small scratch on the surface of your accountability in cloud security:
- Information and Data: Your provider has zero visibility into your data, and all data access is yours to control by design.
- Identity and Access: You are responsible for all facets of your identity and access management (IAM), including authentication and authorization mechanisms, single sign-on (SSO), multi-factor authentication (MFA), access keys, certificates, user creation processes, and password management.
- Platform and Resource Configuration: When you spin up cloud environments, you control the operating environment. How you maintain control over those environments varies based on whether your instances are server based or serverless. For serverless resources, your provider’s control plane gives you access to the setup of your configuration, and you are responsible for knowing how to configure your instance in a secure manner.
- Application Logic and Code: Regardless of how you choose to spin up cloud resources, your proprietary applications are yours to secure and control throughout the entire application lifecycle.
- Network Access: By default, providers will enable connectivity to your applications over security. It is incumbent on the customer to balance security with connectivity.
The speed of cloud is allowing for DevOps to enjoy significant acceleration in their ability to deploy and evolve cloud-based applications. This acceleration, however beneficial for innovative potential, is often connected to your production assets and can pose significant security risks if not properly configured. Unfortunately, that also means your DevOps pipeline can inadvertently and rapidly introduce security vulnerabilities without proper consideration and management. Gartner states that misconfiguration accounts for 99% of cloud security failures. As all of this change takes places, a more foundational goal is to make security and compliance part of the development process from the start. Centralized, automated access management and policy-driven environment creation are critical for the success of your cloud security implementation.
How can “we” close the gap?
Putting the shared security concept into practice for your cloud workloads requires assessing the details of the way those workloads are configured. The fact that many organizations now use multiple clouds at once can also complicate shared responsibility, especially if some of their workloads run in a public cloud and others run in a private cloud. Your operations team needs to work closely with security to maintain policy-based control over how and when your cloud resources are provisioned. The potential solution to managing and keeping all this fast-paced movement under control is Software-Defined.
The speed and ease of configuring software-defined infrastructure will open your company up to new levels of agility and adaptability. Software-Defined Networking or SDN is a number of technologies wrapped up into a tidy package. It features Software-Defined overlays that are separate from any underlying hardware, which results in a network that gives you faster, automated provisioning and top-level security.
In the past, we went for high availability and redundancy, and we left security to deal with later. We can’t afford to leave security as an afterthought. Through scripting, automation, and carefully planned self-service workflows, your configuration management and security teams can work together to give your company controlled, secure access to the cloud resources they need without becoming a bottleneck.
Our history as an implementer and infrastructure managed service provider positions us perfectly to close the gap in the shared responsibility model. Our roots are deep; deep in networking, security, collaboration, applications - all of the critical elements to understanding how security impacts your operations. We have introduced patented connectivity and security products with CloudConductor™, while working with our chosen manufacturers to keep ahead of the curve. We enable our customers to find the right balance of security and usability to deliver on the best experience possible.
It’s not enough to just understand cloud, you have to understand the access methods as well. Core technologies like SASE, SDN, Zero Trust play a key role into bridging the gap between securing native cloud applications and hybrid/legacy server infrastructures.


